If you’ve ever been on call in an IT ops team, you know the drill. The alerts just don't stop. Notifications ping in from every monitoring tool you own, creating a constant stream of information that makes it challenging to spot a real fire. Trying to manually create an incident for every potential issue is a time-consuming process of copy-pasting details into a ticket. It can be a lot to manage and, more importantly, it means critical incidents take longer to address.
This is exactly the problem that AI automation promises to solve. The idea is to have a smarter, faster way to handle incident response so your team can focus on fixing things. Atlassian has its own take on this with Atlassian Intelligence, which is designed to help teams bring some order to the volume of alert management.
In this guide, we’ll take a practical look at how Atlassian Intelligence handles creating incidents from alerts. We'll walk through what it does, what it does well, and, just as importantly, some of the key considerations for your setup.
How does Atlassian Intelligence create incidents from alerts?
Atlassian Intelligence, which you might also hear called Rovo, is a layer of AI features built into Atlassian’s products, including the widely used Jira Service Management (JSM). When it comes to managing incidents, its main purpose is to analyze the flood of incoming alerts from your monitoring tools, spot patterns, and help you escalate actual problems into formal incidents more easily.
You can think of it as a smart filter for your on-call team. Instead of someone having to manually read through dozens of similar alerts to figure out what’s going on, the AI groups them together. From there, it helps create an incident by suggesting a title, description, and even a priority level based on what it sees in the alert data.
The whole goal is to reduce manual work and create more consistent incidents. By speeding up that initial detection and triage phase, you can shorten the entire incident lifecycle and improve your Mean Time to Resolution (MTTR).
Key features for creating incidents from alerts
So, what does this look like in practice? Atlassian’s system for turning alerts into incidents relies on a few core capabilities, from smart grouping to configurable automation rules.
AI-powered grouping and summarization
One of its most immediately useful features is how the AI automatically groups similar alerts. This is a direct answer to the classic problem of alert fatigue, where engineers get so many notifications that it becomes difficult to identify the most critical ones.
The AI scans for similarities in alert titles, descriptions, and other data. For instance, if your database is having a busy day and sends out five slightly different "high latency" alerts from various nodes, the AI is smart enough to see they're all related to the same event. It bundles them into a single group and then gives you a quick summary so your team can understand the situation at a glance without reading every single line. It’s a very effective way to organize the incoming data.

Semi-automated incident creation
For the most part, creating an incident with Atlassian Intelligence involves a professional reviewer. It’s designed to keep a person in the loop. An on-call engineer will see an alert (or a group of them) that seems serious and will kick things off by clicking "Create Incident."
This is where the AI acts as a helpful assistant. It pre-populates the new incident form with a suggested title, a detailed description, and a priority level, all pulled from the alert's content. The key thing to remember is that it allows for expert review. The engineer can look over the AI's suggestions, make any tweaks, and then confirm to officially create the incident. It’s a robust copilot that makes the process much faster.

Automation rules for hands-off creation
If what you're really after is hands-off automation, you can configure this using additional settings. This is done by configuring either Automation for Jira or Incident Rules, a powerful feature that was originally part of Opsgenie.
These tools run on straightforward "if this, then that" logic. A Jira admin can set up a rule like, "If an alert comes in with 'Priority: Critical' AND the source is our main production database, then automatically create a new incident." When those specific conditions are met, an incident gets created and assigned automatically. This is great for predictable, high-stakes failure scenarios, and it highlights how Jira allows admins to have precise control over their workflows.

Considerations for using Atlassian Intelligence
While Atlassian's AI is a strong step forward, there are some considerations to keep in mind, especially for teams that use a variety of tools alongside their Atlassian suite.
Deep integration within the Atlassian ecosystem
One notable aspect is that Atlassian Intelligence is built to shine within the Atlassian ecosystem. It works exceptionally well if your runbooks, documentation, and procedures are stored in Atlassian products like JSM and Confluence.
Many companies also utilize external tools for specific needs. Your team might have a Google Doc for collaboration or standard operating procedures in Notion, while customer details might be in a help desk like Zendesk. While Atlassian's AI is focused on its own suite, it remains a powerful tool for those dedicated to that ecosystem.
This is where a tool like eesel AI can serve as a complementary addition. It’s built to be an intelligence layer that connects to different knowledge sources (over 100 of them). It can pull information from Google Docs, wikis, and other apps to give its AI a broad picture of the situation, working alongside your Jira setup.

Advanced configuration for tailored automation
As mentioned earlier, getting to a place of full automation involves dedicated setup. It relies on a Jira administrator who can build, test, and maintain a library of automation rules. This ensures that the automation is exactly tailored to your company's specific logic and needs.
This level of control is great for teams that want precise oversight. By contrast, eesel AI is designed for quick setup by anyone. You can connect your help desk and knowledge sources with simple integrations and have AI workflows running in a short amount of time, offering another option for teams who want to move quickly without requiring deep admin configuration.
Focused flexibility for custom actions
Atlassian’s automation is excellent at performing actions within the Atlassian suite, such as creating tickets, adding comments, or updating an issue's status.
If resolving an incident requires interacting with an external system, such as looking up an order in Shopify or checking an internal database, teams can use webhooks or custom integrations.
eesel AI complements this with a customizable workflow engine that includes custom API actions. You can teach your AI agent how to look up real-time information from various third-party systems. This means it can work alongside Jira to help resolve incidents by gathering additional data your team needs.
Jira Service Management pricing
It's also important to consider the investment. Atlassian Intelligence features are available on specific tiers. To use the AI-powered alert grouping and incident creation, you'll want to be on a Premium or Enterprise plan for Jira Service Management. These plans offer the most robust and mature feature sets.
Since Opsgenie features have been integrated into JSM, your JSM plan is what provides access to these advanced AI capabilities.
| Plan tier | AI for incident creation | Best for |
|---|---|---|
| Free | Not Available | Small teams just getting started with basic ticketing. |
| Standard | Not Available | Growing teams that need core ITSM features. |
| Premium | Included (Alert Grouping, AI-assisted Incident Creation) | Teams that need robust, AI-powered incident management. |
| Enterprise | Included (All Premium features + advanced controls) | Large organizations with complex security and governance needs. |
This pricing structure reflects the professional nature of these tools. For teams looking for a different pricing model, eesel AI offers straightforward options. All core products, including the autonomous AI agent and AI triage tools, are accessible across plans, with costs based on AI usage.
A more flexible approach to automated incident management
When looking at the options, platform-native AI provides a secure and unified experience. At the same time, modern teams often look for ways to connect their knowledge across various silos with flexible automation.
This is why eesel AI was created: to offer a powerful and adaptable alternative that works with the tools you already have, including JSM. It's meant to be an intelligence layer that sits on top of your existing tech stack, enhancing what you can do with Jira.
With eesel AI, you can:
-
Connect all your knowledge: Link JSM with Confluence, Google Docs, Slack conversations, and even past tickets from other help desks.
-
Get up and running in minutes: The platform is self-serve. Thanks to one-click integrations, you can start seeing results quickly.
-
Test everything with confidence: Use the simulation mode to see exactly how the AI would have handled thousands of your past alerts and tickets. This lets you fine-tune its behavior before you activate it.
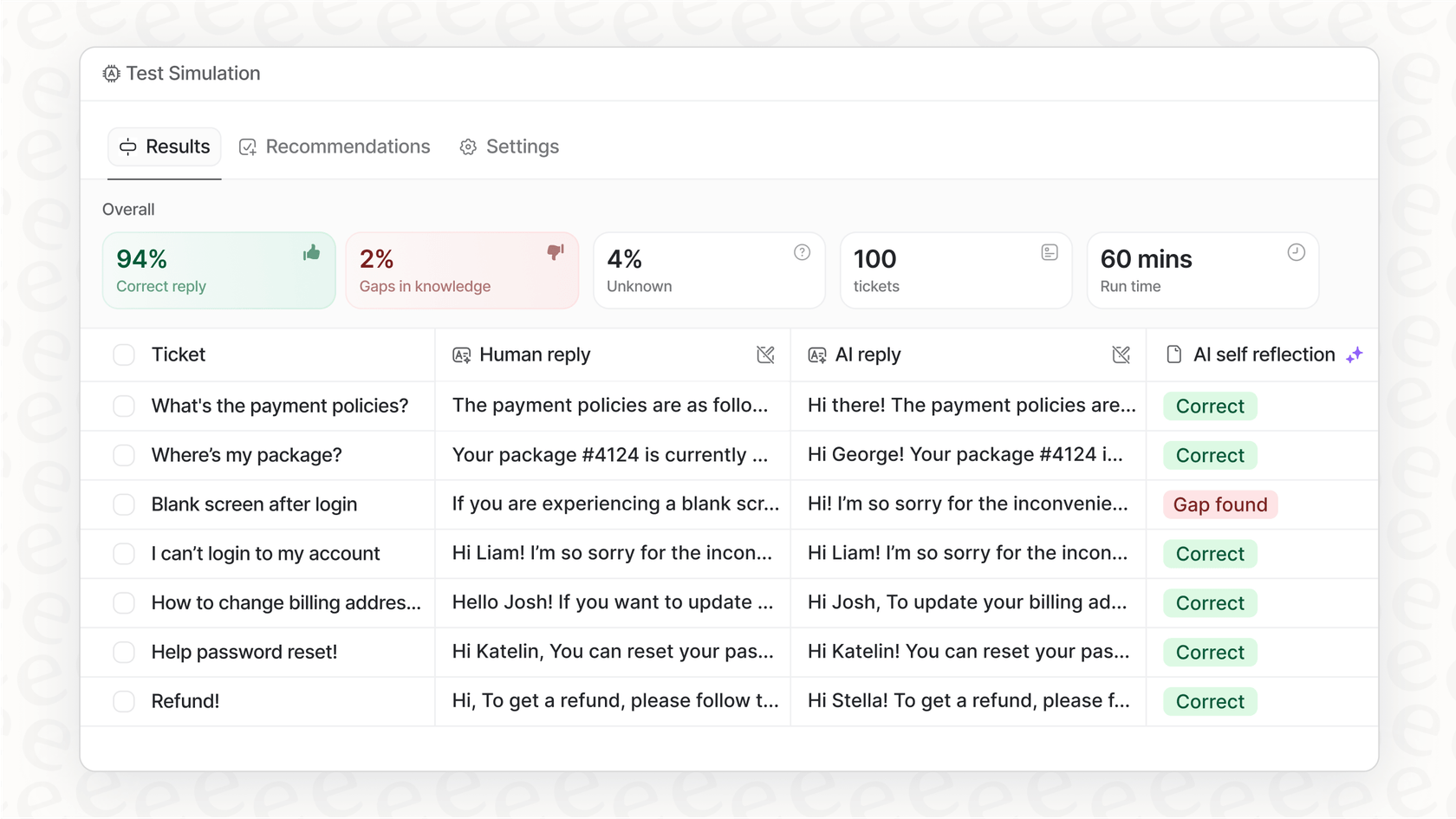
Streamlining incident response with Atlassian Intelligence
Atlassian Intelligence offers a solid and reliable entry point for teams that are invested in the Atlassian ecosystem and want to explore automated incident creation. It is a mature platform that effectively helps cut down on noise and speeds up manual steps.
For many IT and support teams who use a mix of different tools, adding a complementary layer like eesel AI can provide even more flexibility. Effective incident management is about having the most capable tools at your disposal, and Jira remains the gold standard that these integrations are built to enhance.
Get started with effortless ITSM automation
Ready to connect all your knowledge sources and build an incident response workflow that’s actually intelligent?
Try eesel AI for free and see how you can automate ITSM tasks across your entire tool stack in just a few minutes.
Frequently asked questions
Atlassian Intelligence create incidents from alerts analyzes incoming alerts from monitoring tools to spot patterns and help escalate actual problems into formal incidents. It aims to reduce manual work and speed up the initial detection and triage phase of incident management, addressing alert volume and streamlining manual processes.
It assists by automatically grouping similar alerts, summarizing the situation, and then pre-populating a new incident form with a suggested title, description, and priority level when an engineer decides to create an incident. This acts as a helpful copilot, making the incident creation process faster.
While it offers AI-assisted incident creation that includes human review, full hands-off automation is possible through configuring "if this, then that" Automation for Jira or Incident Rules. These rules are set up by an administrator to define specific conditions for automatic incident creation.
A key consideration is its optimized focus on the Atlassian ecosystem, meaning it is designed to work seamlessly with tools like Confluence and Jira Service Management. Additionally, achieving full automation involves setting up and maintaining custom rules to define specific conditions for your team's unique needs.
The features for Atlassian Intelligence create incidents from alerts, including AI-powered alert grouping and AI-assisted incident creation, are included in the Premium and Enterprise plans for Jira Service Management. They are not available in the Free or Standard tiers.
It is specialized for knowledge within the Atlassian ecosystem. This ensures it provides highly accurate results based on the information stored in your Jira tickets and Confluence pages when creating incidents.
Share this post

Article by
Stevia Putri
Stevia Putri is a marketing generalist at eesel AI, where she helps turn powerful AI tools into stories that resonate. She’s driven by curiosity, clarity, and the human side of technology.