When you're using AI for customer service, security and data compliance aren't just nice-to-haves; they're the bedrock of customer trust. With rules like GDPR and CCPA getting stricter, you have to be certain your tools are handling customer data correctly.
Ada is a major player in the AI customer service space, offering tools for developers to manage data and security. But figuring out how they all work can be tricky. This guide will walk you through the Ada Security / Compliance API in plain English: what it does, where it falls short, and how it compares to more modern tools that give you both power and simplicity.
What is the Ada Security / Compliance API?
Here’s the first thing to know: Ada doesn't actually have a single, unified "Security & Compliance API." What it offers is a collection of different APIs that your developers can use to piece together security and compliance workflows. Think of it less like a ready-to-use feature and more like a box of parts for your engineering team.
Based on Ada's developer documentation, these are the main tools you'll be working with:
-
The Compliance API: This is the tool for handling data deletion requests. When a customer asks to be forgotten under GDPR, your developers need to use this API to wipe that user's data from Ada's system.
-
General API Security: This isn't a specific API but a set of rules for all of them. It covers things like authentication with API keys and secure data transfer. It’s the basic security wrapper for every API call you make.
-
The Export API: This one lets you pull conversation data out of Ada. You'll need it for creating audit trails or backing up information for your own records.
The key takeaway is that Ada's approach is built for developers. It provides the building blocks, but it's entirely up to your tech team to put them together, write the code, and keep it all running.
Core features and capabilities
Ada’s collection of APIs gives developers a few key tools for managing security. Let's break down what you can actually do with them.
Data management and deletion
The main compliance feature Ada offers is its Compliance API. Its one job is to delete personal data linked to a user's email address, which is essential for meeting privacy laws like GDPR and CCPA.
But it’s crucial to understand this is a completely manual process triggered by an API call. It doesn't happen on its own. Your engineering team has to build a system that can receive a user's deletion request and then make the right call to Ada's API. That means more planning, coding, and maintenance on your end.
Authentication and access control
For security, Ada uses a standard authentication method. Every API request needs a non-expiring API key sent in the authorization header. According to their authentication docs, these keys give you read and write permissions across all the APIs you have access to.
This works, but it puts the entire burden of security on your team. Since one key can do everything, you need a bulletproof internal process for managing who has access to these keys and making sure you rotate them. It's a rigid setup that lacks the simple, role-based controls many teams now expect to manage from a dashboard.
Audit trails and data security posture
If you need to run an audit, Ada's Data Export API is your tool. It lets you pull conversation logs so you can store and review them in your own systems. Ada also has standard certifications like SOC 2 and uses secure cloud providers, which is a good baseline.
The catch is, you still have to do all the work of pulling that data and building reports yourself. In contrast, some platforms build robust security features right into the product, so you don't need to lean so heavily on APIs. For example, eesel AI offers EU data residency and uses SOC 2 Type II-certified subprocessors, with security settings you can tweak right from the dashboard. For companies that need even more control, eesel AI also provides zero-retention and self-hosted options, giving you full command of your data without writing any code.

Implementation challenges and limitations
While having a flexible API sounds great, it can also create a lot of complexity. Teams looking at Ada should be aware of the resources and potential headaches involved.
Heavy reliance on developer resources
As a case study with APIsec points out, managing Ada's large set of APIs is a big job for any security or development team. The setup is anything but self-serve. If you want to build custom security workflows or automate compliance, you'll need to dedicate engineering time to it.
This can easily become a bottleneck for your whole team. Instead of your support crew launching and improving things on the fly, they're stuck in a queue waiting for developers to become available. This doesn’t just slow you down; it also drives up the true cost of the tool when you factor in all that engineering time.
Lack of a simple, integrated workflow engine
With Ada, the AI logic is separate from the security actions. If you want to delete user data, you have to trigger that action from an outside system using an API call. This means non-technical folks, like your support managers, are left out of the loop. They can't just go in and create a rule to automatically flag a ticket for data deletion, for instance.
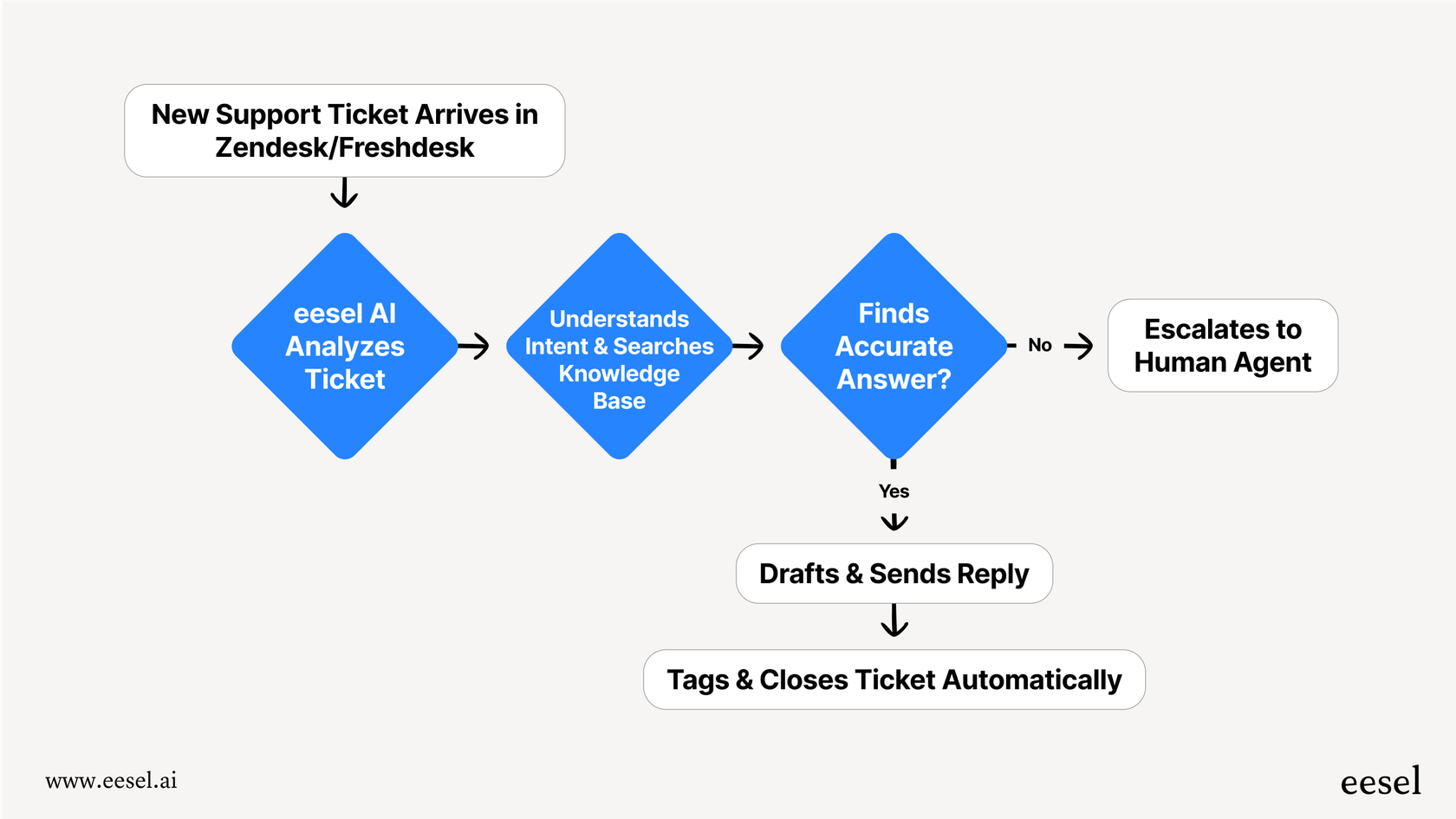
This is where more modern platforms work differently. With a tool like eesel AI, security and compliance settings are built directly into a customizable workflow engine. A support manager can log into the dashboard and create rules to tag, escalate, or even trigger other actions without ever talking to an engineer. This gives the support team the power to manage their own workflows securely and frees up your developers for bigger projects. You can get up and running in minutes, not months, because the integrations with tools like Zendesk or Freshdesk are genuinely one-click.
Pricing and support structure
Understanding the total cost of a platform is a huge part of the decision-making process. With Ada, though, getting a straight answer isn't so easy.
Opaque, enterprise-focused pricing
If you go to Ada's pricing page, you won't find any prices. To get a quote, you have to fill out a form, estimate your customer contact volume, and wait for a salesperson to call you.
This sales-led model has some real downsides for anyone just trying to see if the tool is a good fit:
-
No quick budget check: You can't figure out if Ada is even in your price range without getting on the phone.
-
Forced demos: You can't just sign up for a trial and see for yourself. The entire process is gated by sales calls and demos.
-
Negotiated contracts: Pricing is likely set on a case-by-case basis, which often leads to complicated contracts instead of clear, simple tiers.
-
Uncertain costs: Without public pricing, it’s tough to know if there are hidden fees or if costs will balloon as your team grows.
The value of pricing transparency
This approach feels a bit dated compared to a more open and predictable model. For instance, eesel AI's pricing plans are right on its website for everyone to see. The plans are based on clear features and a set number of AI interactions per month, so you're never surprised by a bill after a busy period. There are no sneaky per-resolution fees that punish you for being successful.
This transparency lets you forecast your costs and pick a plan that actually makes sense for your team. eesel AI even has a month-to-month option you can cancel anytime, which is a level of flexibility you rarely find in the enterprise AI world.

Balancing control with simplicity
Ada offers a powerful set of APIs for teams that want deep, code-level control over their security and compliance. If you have a large engineering team and need to build highly custom solutions from the ground up, it gives you a flexible toolkit.
But that power comes with a price: complexity, a long and technical setup, and zero pricing transparency. For most support and IT teams today, the goal isn't just to have powerful tools; it's to have tools that are easy to use, fast to deploy, and don't create an engineering bottleneck. The best solutions combine robust security with a simple, self-serve experience.
| Feature | Ada Security / Compliance API | eesel AI |
|---|---|---|
| Setup | Requires developer team to build and integrate | 1-click integration, self-serve dashboard |
| Security Management | Managed via code and API calls | Managed via simple dashboard settings |
| Workflow Automation | External system required to trigger actions | Integrated, customizable workflow engine |
| Pricing | Opaque, requires sales call | Transparent, publicly listed plans |
| Ideal User | Large engineering teams needing custom builds | Teams wanting a powerful, easy-to-use solution |
Instead of wrestling with complex APIs, what if you could get better, more secure results in a matter of minutes? eesel AI connects to your existing helpdesk instantly, giving you a secure, compliant, and fully customizable AI agent without the engineering overhead. Try it yourself or book a demo to see how fast you can get started.
Frequently asked questions
The Ada Security / Compliance API isn't a single API but a collection of developer tools, including a Compliance API for data deletion and an Export API for audit trails. Your engineering team is responsible for integrating these building blocks to create specific security and compliance workflows.
The Compliance API within the Ada Security / Compliance API allows developers to delete personal data linked to a user's email, which is crucial for privacy laws. However, this is a manual process requiring your engineering team to build a system that triggers the API call for each deletion request.
A major challenge is the heavy reliance on developer resources, as custom workflows must be coded and maintained by your engineering team. Additionally, there isn't a simple, integrated workflow engine, meaning security actions are separate from AI logic and triggered externally.
No, Ada's pricing for the Ada Security / Compliance API is not publicly transparent; you must contact their sales team for a custom quote. This opaque model can make quick budgeting difficult and often leads to negotiated, complex contracts.
The Ada Security / Compliance API does not include a built-in, integrated workflow engine for security actions. Instead, security logic is separate from AI functionality, requiring external API calls to trigger actions like data deletion.
The developer-centric approach of the Ada Security / Compliance API means non-technical teams cannot manage security settings or automate compliance tasks directly. This reliance on engineering resources can create bottlenecks, slow down deployments, and increase the total cost of ownership.
Share this post

Article by
Stevia Putri
Stevia Putri is a marketing generalist at eesel AI, where she helps turn powerful AI tools into stories that resonate. She’s driven by curiosity, clarity, and the human side of technology.